Telegram-Based “Sneaky 2FA” Phishing Kit Targets Microsoft 365 Accounts
hackread.comSneaky 2FA: New Phishing-as-a-Service targets Microsoft 365, leveraging sophisticated evasion techniques and a Telegram-based platform to steal credentials.
In December 2024, during routine threat hunting activities, Sekoia.io uncovered a new Adversary-in-the-Middle (AiTM) phishing kit specifically targeting Microsoft 365 accounts. This phishing kit, dubbed Sneaky 2FA, has been circulating since at least October 2024, with potential compromises identified through Sekoia.io telemetry.
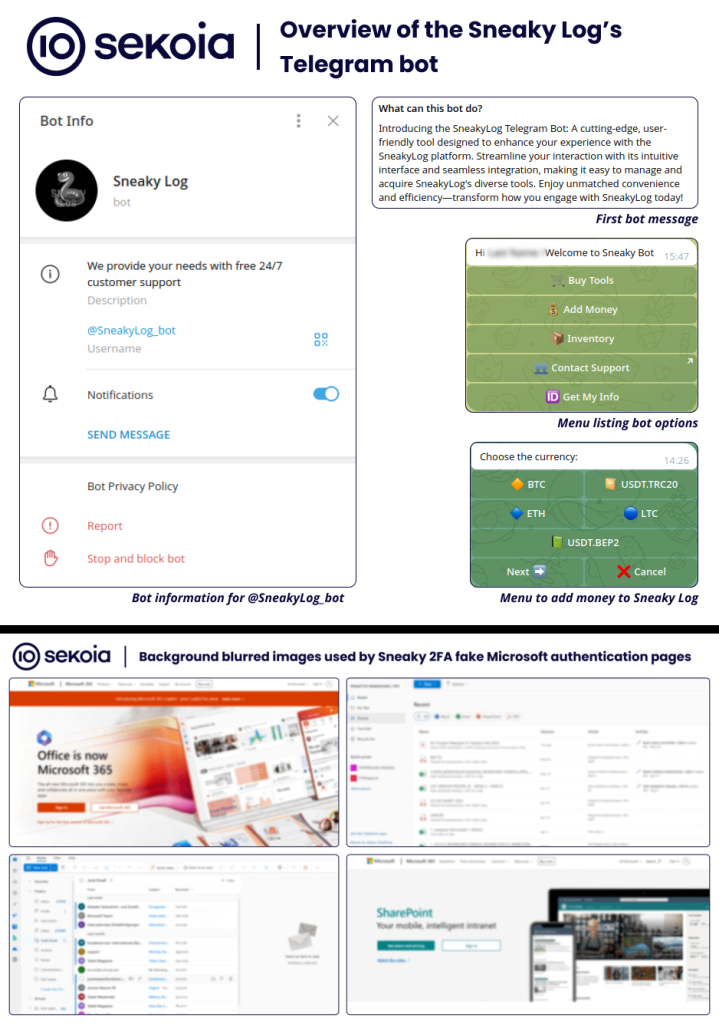
Further probing revealed that Sneaky 2FA is being offered as a Phishing-as-a-Service (PhaaS) by the cybercrime service “Sneaky Log,” which operates through a fully-featured bot on Telegram.
The modus operandi of the entire campaign includes customers receiving access to a licensed and obfuscated source code version, allowing them to independently deploy phishing pages, typically hosted on compromised infrastructure, frequently involving WordPress websites and other domains controlled by the attackers.
In addition, the Sneaky 2FA ...
Copyright of this story solely belongs to hackread.com . To see the full text click HERE