BPFDoor Malware Uses Reverse Shell to Expand Control Over Compromised Networks
gbhackersA new wave of cyber espionage attacks has brought BPFDoor malware into the spotlight as a stealthy and dangerous tool for compromising networks.
According to security experts at Trend Micro, BPFDoor is a state-sponsored backdoor attributed to the advanced persistent threat (APT) group known as Earth Bluecrow (also referred to as Red Menshen).
This malware exploits reverse shells and sophisticated Berkeley Packet Filtering (BPF) techniques to infiltrate and control systems across telecommunications, finance, and retail sectors in regions such as South Korea, Hong Kong, Myanmar, Malaysia, and Egypt.
Understanding BPFDoor Malware
BPFDoor, a backdoor detected as Backdoor.Linux.BPFDOOR, is uniquely powerful due to its reliance on BPF, a kernel-level packet filtering technology.
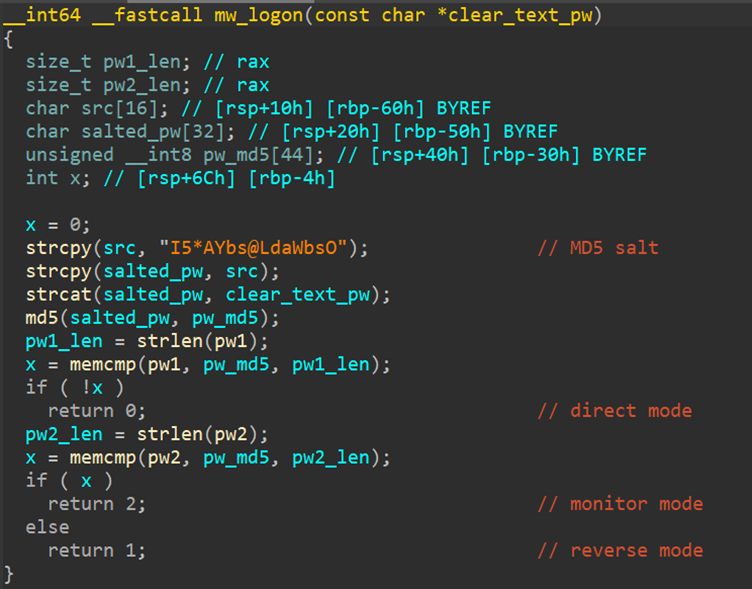
While its core functionalities resemble rootkits, BPFDoor distinguishes itself through its ability to remain undetected by firewalls and evade conventional network scans.
The malware activates upon receipt of “magic sequences ...
Copyright of this story solely belongs to gbhackers . To see the full text click HERE



